There are many “hackers” around the world, some are good and some are bad. Evil, either hacked for money, stolen or just for fun. They like to create havoc or spread malware in the cyber world. Good can also be hacking for money, but in the right way, such as participating in a bug bounty program, helping others to backup lost data, or knowing what vulnerabilities to educate administrators Exist, etc. What does the hacker mean here. Not limited to only those who are able to enter restricted access. He is an IT specialist with the ability to manage a company’s asset security.
Hackers want to be anonymous and difficult so that they can be detected while working. Devices can be used to hide the identity of the hacker from being exposed. VPN (Virtual Private Network), Proxyservers and RDP (Remote Desktop Protocol) are some tools to protect their identity.
To reduce the possibility of penetration testing anonymously and detection detection, hackers need to use an intermediary machine whose IP address will be left on the target system. This can be done using a proxy. A proxy or proxy server is a dedicated computer or software system running on a computer that acts as an intermediary between the end device, such as a computer and another server requesting any services from the client is. By connecting to the Internet through a proxy, the client IP address will not be shown, but rather the IP of the proxy server. This can provide more privacy to a client, if only connecting directly to the Internet.
In this article, I will discuss the Anonymous service built in Kali Linux and or other penetration testing based systems, which are proxins.
PROXYCHAINS FEATURES
- Support SOCKS5, SOCKS4, and HTTP CONNECT proxy servers.
- Proxychains can be mixed up with a different proxy types in a list
- Proxychains also supports any kinds of chaining option methods, like: random, which takes a random proxy in the list stored in a configuration file, or chaining proxies in the exact order list, different proxies are separated by a new line in a file. There is also a dynamic option, that lets Proxychains go through the live only proxies, it will exclude the dead or unreachable proxies, the dynamic option often called smart option.
- Proxychains can be used with servers, like squid, sendmail, etc.
- Proxychains is capable to do DNS resolving through proxy.
- Proxychains can handle any TCP client application, ie., nmap, telnet.
PROXYCHAINS SYNTAX
Instead of running a penetration test tool, or creating multiple requests to any target directly using our IP, we can let Proxychains cover and handle the job. Add command “proxychains” for every job, that means we enable Proxychains service. For example, we want to scan available hosts and its ports in our network using Nmap using Proxychains the command should look like this:
proxychains nmap 192.168.1.1/24 |
Lets take a minute to break up the syntax above:
– proxychains : tell our machine to run proxychains service
– nmap : what job proxychains to be covered
– 192.168.1.1/24 or any arguments needed by certain job or tool, in this case is our scan range needed by Nmap to run the scan.
Wrap up, the syntax is simple, as it is only adds proxychains on start of every command. The rest after the proxychain command is the job and its arguments.
HOW TO USE PROXYCHAINS
Before we are using proxychains, we need to setup proxychains configuration file. We also need a list of proxy server. Proxychains configuration file located on /etc/proxychains.conf
Open proxychains.conf file in your desirable text editor and set up some configuration. Scroll down until you reach the bottom, at the end of file you will find:
[ProxyList] |
# add proxy here ... |
# meanwile |
# defaults set to "tor" |
socks4 127.0.0.1 9050 |
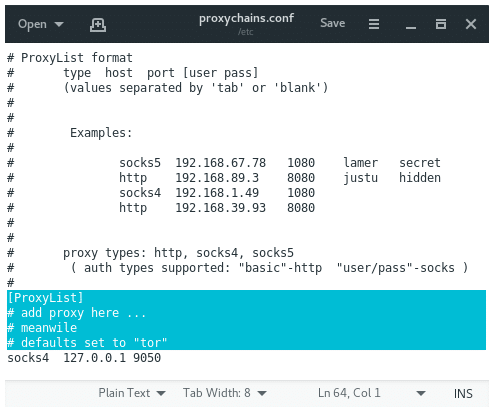
By default proxychains directly sends the traffic first through our host at 127.0.0.1 on port 9050 (the default Tor configuration). If you are using Tor, leave this as it is. If you are not using Tor, you will need to comment out this line.
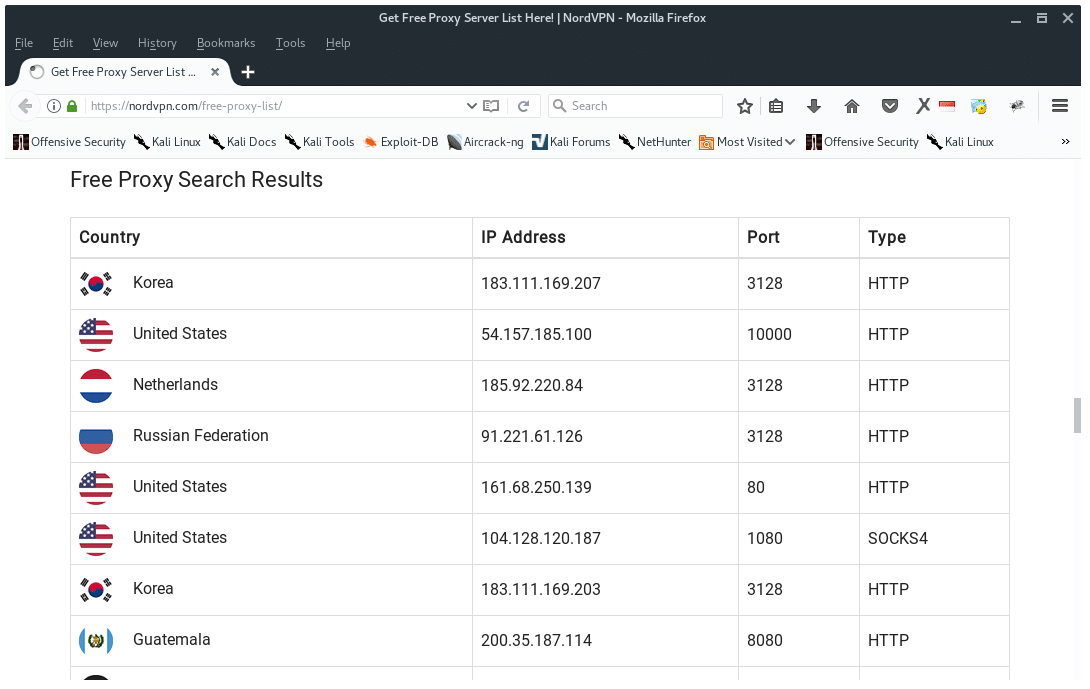
Now, we need to add more proxies. There are free proxy servers on the Internet, you may look at Google for it or click this link Here I am using NordVPN free proxy service, as it has very detailed information on their web site as you see below.
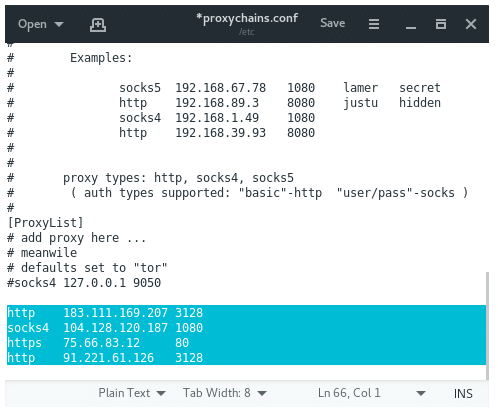
Comment the default proxy for Tor if you are not using Tor then add the proxy on Proxychains config file, then save it. it should look like this:
DYNAMIC_CHAIN VS RANDOM_CHAIN
Dynamic chaining will enable us to drive our traffic through each proxy on our list, and if one of the proxies is down or not responding, the dead proxy is omitted, it will automatically create an error. Will go to the next proxy on the list without throwing. Each connection will be chained behind the scenes. All the proxies will be chained in order as they appear in the list. Activating dynamic channing allows for a more anonymous and hassle-free hacking experience. To enable dynamic chaining in the configuration file, uncomplement the “dynamic_chans” line.
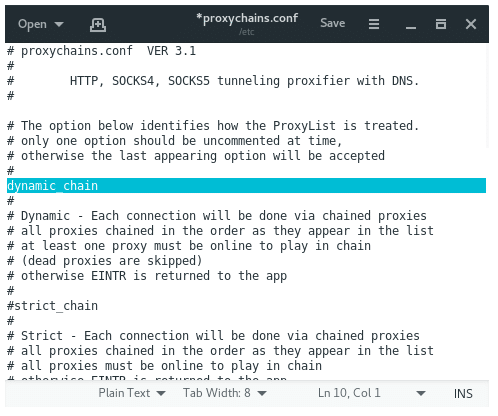
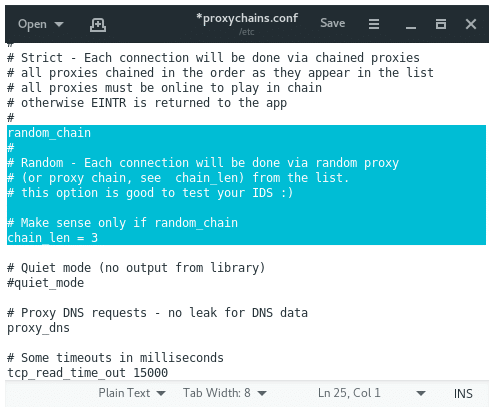
Random chaining will allow proxychins to randomly select IP addresses from our list and every time we use proxychins, the chain of proxies will look different from the target, making it harder to track our traffic from its source.
Enable random chaining comment to unconfigure “dynamic chain” and “random chain”. Since we can only use one of these options at a time, make sure that you comment on the other options in this section.
You may also want to uninstall the line with “chain_len”. This option will determine how many IP addresses of your chain will be used to create your random proxy chain.
Ok, now you know how hackers use proxychains to cover their identity and stay anonymous without worrying about being detected by target IDS or forensic investigators.











Like!! Really appreciate you sharing this blog post.Really thank you! Keep writing.
I loved as much as you’ll receive carried out right here.
The sketch is tasteful, your authored subject matter stylish.
nonetheless, you command get got an nervousness over that you wish be delivering the following.
unwell unquestionably come further formerly again since exactly the same nearly very often inside case you shield this hike.
I do not even know how I ended up here, but I thought
this post was good. I do not know who you are but definitely you are going to a
famous blogger if you are not already 😉 Cheers!
Hmm is anyone else encountering problems with the pictures
on this blog loading? I’m trying to determine if its a problem on my end or if it’s the blog.
Any feed-back would be greatly appreciated.
Having read this I thought it was extremely informative.
I appreciate you spending some time and effort
to put this short article together. I once again find myself personally spending
a significant amount of time both reading and commenting. But so what,
it was still worth it!