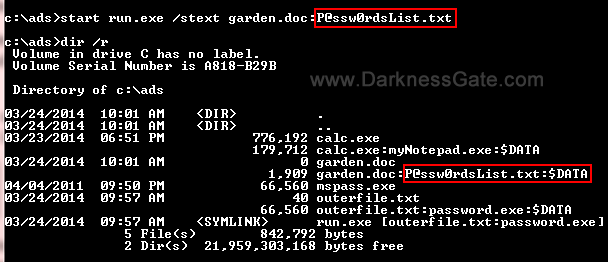
EvilApp – Phishing Attack Using An Android App To Grab Session Cookies For Any Website (ByPass 2FA)
A man-in-the-middle phishing attack using the Android app to grab session cookies for any website, which in turn allows to bypass 2-factor authentication security. EvilApp brings as an example the hijacking and injection of cookies for authenticated Instagram sessions. Legal disclaimer: Usage of EvilApp for attacking targets without prior mutual consent is illegal. It’s the…










![[DeNA formula] Article mass production SEO method [I will explain in 5 steps] DeNA seo](https://www.itjd.in/wp-content/uploads/2021/11/DeNA-seo.jpg)